Tailscale & Pomerium: Better Together

Tailscale is an encrypted network mesh that allows you to connect devices across different networks and make them accessible from anywhere in the world. Many of Tailscale’s customers use them to simplify networking and replace the traditional VPN.
Pomerium is an open-source identity and context-aware proxy that provides secure access to internal applications. Pomerium’s customers want to shift away from the VPN and gain conditional per-request access and fine-grained logging capabilities.
By combining their capabilities, you can couple Tailscale’s encrypted network mesh with Pomerium proxy to securely access internal applications and networks. This combination ensures that your internal applications are accessed securely and privately even if those applications are hard to reach because they are hosted on a network behind a NAT.
Organizations already using Tailscale will want to put Pomerium in front of their Tailscale networks to gain better fine-grained auditing and logging capabilities and conditional per-request access.
What’s The Use?
Tailscale is really good at what they do, and what they do is effortlessly connect networks together. By stitching various networks into one, Tailscale provides organization network administrators the ability to provision access to any service within all these connected networks, allowing for direct connections without the need for complicated setups.
But being a next-gen VPN replacement has its downsides: Tailscale cannot escape some of the fundamental problems that plague VPNs. Layer 4 tools protect connections and packets, making them agnostic to the type of data they are protecting.
Pomerium comes in to do what Tailscale cannot: a layer 7 proxy to provide continuous verification and fine-grained logging and auditing capabilities by examining and enforcing policy on every single request.
Adding Continuous Verification
As a “NextGen” VPN, Tailscale is still vulnerable to the fundamental issue plaguing VPNs: a built-in assumption that everything inside can be trusted and everything outside is untrusted.
While Tailscale comes with the default authentication, authorization, and Network Access Controls (ACLs) we should expect from any VPN solution, this isn’t enough for the modern threat landscape. Although Tailscale is great at providing access across networks, it is poor at securing and monitoring the activities performed with that access.
- Compromised credentials are the most common attack vector with an average cost of $4.5 million per breach
- Negligent or criminal insiders cost $6.6 and $4.1 million respectively
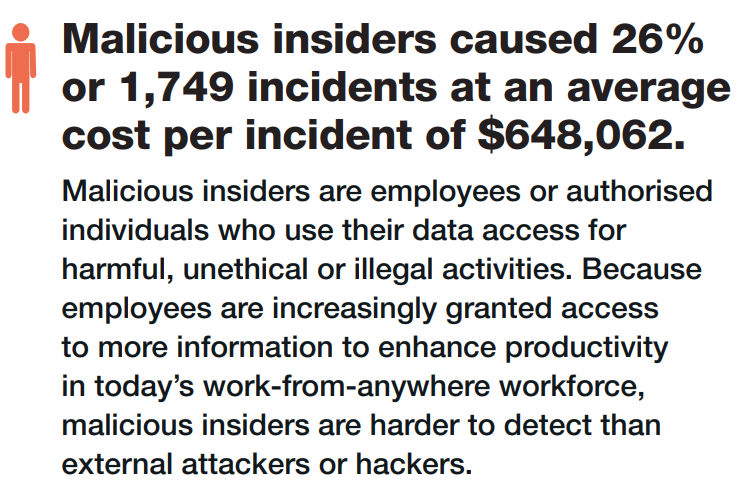
Tailscale’s access control capabilities cannot mitigate these two costly examples, one being the most common attack vector.
Continuous verification evaluates every single action and request by each user against access policy before access is granted. This is a large departure from Tailscale checking users in at the gate and hoping the IT team has effectively cordoned off the internal network with a complex series of firewalls.
Pomerium brings continuous verification to your tailnet. More advanced organizations may want to put Pomerium in front of each individual resource in their network, ensuring that each resource gains authentication and authorization capabilities and is less reliant on the network’s own security.
Better yet, you also gain…
Fine-grained logging and auditing
Pomerium’s ability to log every single request and action taken in your network is a core reason why so many Tailscale users add Pomerium on top of their tailnet. Here’s a comparison of the logs:
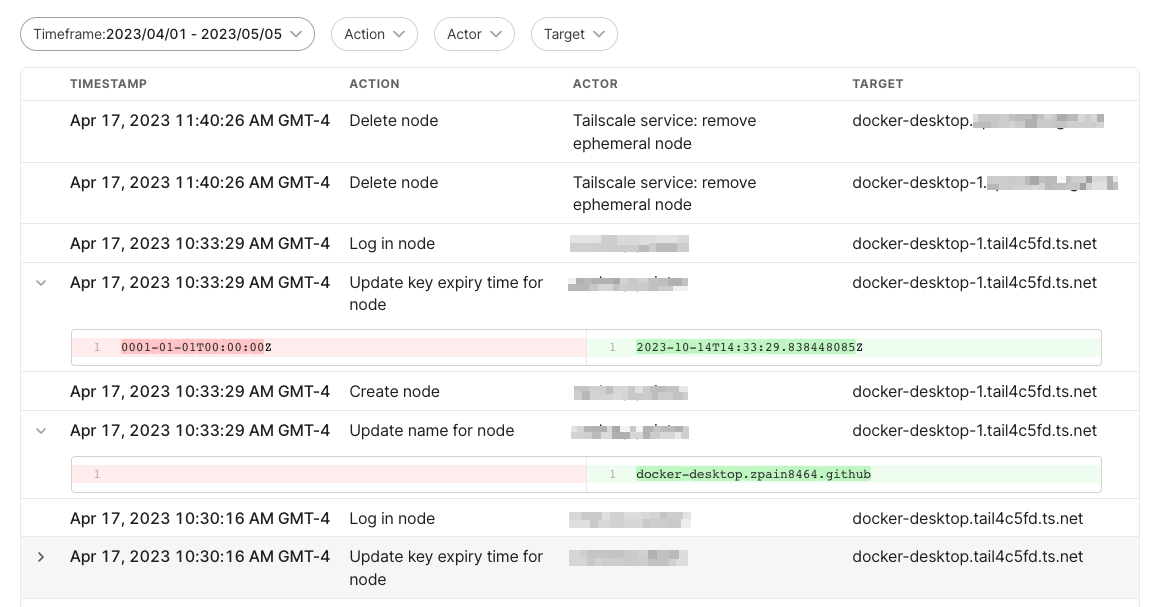
Tailscale’s logging tells us four things:
- Who did it?
- When did it happen?
- What happened and what was acted upon?
- Where did this action take place?
At first glance, this seems enough. After all, it provides answers to 4 out of 5 commonly asked questions. On paper (and in the past), this log would be enough for auditing. But as children know, “Why?” is an important question.
When it comes to security auditing, you really want to know more than just who what when and where. Why did the mechanisms in your access control allow or deny the action, based on what? This will prove to be useful for administrators when diagnosing why a user can’t gain access to a resource (or even why they can/did). Unfortunately, Tailscale is a Layer 4 tool and therefore unable to provide these logs without Pomerium.
More granular logging is why (heh) users add Pomerium. Take a look:
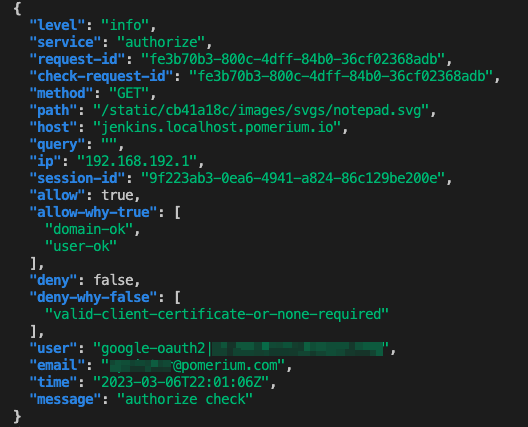
Pomerium’s logging includes everything Tailscale has and more: verifying what it thinks to be known, and the why. Audit logs should provide full visibility into every single request taken on the network, who what when where why and very importantly, how.
Not just limitations, but also gaps
Their own documentation lists out their limitations, but here it is copied (as of May 16, 2023), with Pomerium easily addressing all items marked in purple.
- Configuration audit logs only include actions that modify a tailnet’s configurations. Read-only actions, such as a user viewing the admin console, are not included.
- Changes to a tailnet that were initiated by Tailscale’s support team are not currently included.
- Configuration audit logs only include changes to configuration of a tailnet. Information about connections within a tailnet (data plane audit logs), such as network flow logs, are not included in configuration logs. You can use Network flow logs to log information about connections with a tailnet.
- Configuration audit logs are available as part of the admin console, exportable via API, and as a streaming source for SIEM systems.
- There is currently no guarantee for a maximum delay between an event taking place and its inclusion in the audit logs. In practice, this occurs within seconds.
- The period of time that logs are stored cannot be configured. Logs are stored for 90 days.
- Devices with the same node key will appear in logs as the same node target.
- When a user is suspended, the suspension of the user’s nodes, API access tokens, and auth keys are not logged.
- When a user is deleted, the deletion of the user’s API access tokens and auth keys are not logged.
All of these unlogged items — such as the suspension and deletion of users — are critical for auditing trails and ensuring organizations have a good understanding of what is happening in their networks.
Third Party Exposure?
This one is curious: “Changes to a tailnet that were initiated by Tailscale’s support team are not currently included.” This is a direct admission of two things:
- Tailscale’s logging mechanisms treats their support team’s actions differently
- “not currently included” — does this mean they have the capability to include this, but chose not to?
Of course, we’re not insinuating Tailscale means anyone harm. However, security-minded individuals should pay close attention to the flaws of incomplete logging because it inhibits detection and remediation. If Tailscale is ever breached or has a malicious insider, users can be impacted and it is not logged.
It is one thing to accept that Tailscale’s support team has a (perhaps necessary) backdoor into your tailnet — it is another to have absolutely zero insight into what Tailscale is doing with that backdoor access. Third-party vulnerabilities are increasingly difficult to predict despite happening constantly, and organizations are encouraged to do a risk assessment. As it is now, in the event of a breach at Tailscale, there would be no logs or audit trails to understand what malicious actors did with Tailscale’s privileged, unlogged access.
How to Use Pomerium With Tailscale
Pomerium is most useful when running a network of servers using Tailscale. For example, our own developers deploy Pomerium on top of the networks when running services on machines and treating them as servers.
To use Pomerium with Tailscale, you can follow these steps:
- Install Tailscale on your server and client machines: Tailscale provides installation instructions for various platforms on their website.
- Connect your client machines to your Tailscale network: Once you have Tailscale installed on your client machines, you can connect them to your Tailscale network. This will allow you to access your internal applications from these machines.
- Install and configure Pomerium on your server: Pomerium can be easily installed in 5 minutes. You will need to specify the internal applications that you want to make accessible through Pomerium.
- Specify the tailnet endpoint as a
to:, such as:
to: http://1.2.3.4:123Example:

That’s the IP in the tailscale dashboard. Our developer personally adds a DNS entry to their domain, lemur.tailscale.doxsey.net, so it would be to: http://lemur.tailscale.doxsey.net
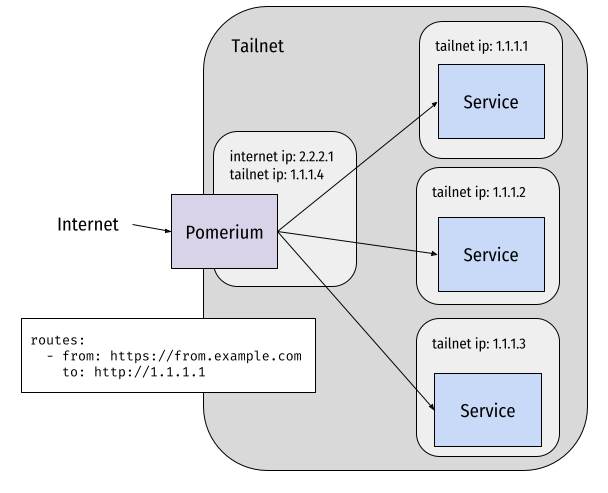
For those who are curious about using Tailscale with Pomerium, here’s an architecture diagram:
Protect More than Just a Tailnet
Pomerium enables secure, identity and context-aware access to any app or resource on any network, not just tailnets. Our proxy is the top choice for companies looking for an open-source context-aware access gateway to manage secure, identity-aware access to applications and services. Customers depend on us to secure zero trust, clientless access to their web applications everyday.
Check out our open-source Github Repository or give Pomerium a try today!


