Our Recommendation
DNG is a reasonable choice if you already use Duo’s other 2FA services for device endpoint authentication, authorization, posture and health checks. The Duo ecosystem feeds into and plays well with itself.
However, DNG forces you to use a SAML-compliant identity provider, limiting companies that have shifted to using OAuth2 or OIDC. We also think that there are better SAML-based SSO options when DNG forces users to log in multiple times.
Teams using OIDC or OAuth2 or not already locked into the Duo ecosystem should use Pomerium for better security posture and usability. For more details, please read our Evaluators Should Know section below.
Evaluators Should Know
Here’s our findings after going through the process of setting up Duo Network Gateway for testing. We base our evaluation on a strict four-pillar criteria when evaluating access control solutions:
Usability: We applaud DNG pushing for clientless access. However, enforcing policy through DNG requires users to install Duo Desktop or Mobile, defeating the clientless feature. Additionally, needing to login multiple times (thus invoking multiple credentials) does not achieve SSO.
Speed: DNG’s speed and latency should be on par with Pomerium’s given that both are reverse proxies that can be deployed at edge.
Security: DNG lacks continuous verification and does not pass credentials upstream, forcing users to sign in multiple times. This is on top of some of their more valuable security features requiring Duo Desktop or Duo Mobile, defeating the purpose of clientless access.
Context-Aware: DNG is capable of detecting anomalous behavior but cannot import unique proprietary data sources.
For the purposes of reproducing our results, we used JumpCloud identity provider and secured Grafana as our the internal application.
Usability
Companies looking for an SSO-solution will not be satisfied by DNG. Duo’s DNG proxy cannot pass user credentials to protected applications, resulting in multiple sign-in processes:
This access flow categorically defeats its intended purpose as a SSO solution, which is intended to reduce password fatigue.
Then there’s clientless access, a major aspect of usability. VPN replacements and access control systems should not require clients when provisioning access. Unfortunately, DNG’s access flow requires Duo Desktop or Duo Mobile — a software installed on the device to perform checks and gate access until you login through their client. This policy requirement defeats the point of clientless access.
Speed
All client-based tunneling solutions will be inherently slower than Pomerium due to data backhauling, so we’re glad to report that DNG does not have this problem. We’re happy to say that when it comes to latency, we expect users to find DNG equally fast with Pomerium.
There is not much to say here besides explaining to decisionmakers how this can be determined without running extensive benchmark tests:
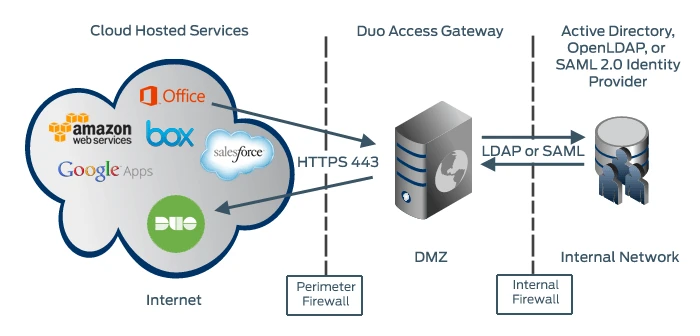
Solutions with VPN-like architecture where there’s an intermediate server passing along data cannot avoid adding an extra “hop,” or travel point, for the data. This physically increases the total distance for data to travel, resulting in additional latency and bandwidth concerns.
Because Pomerium and DNG are both deployed at edge right in front of the service, there are no additional travel points that add to latency.
Security
It is problematic that DNG’s security model does not perform continuous verification, a critical component of zero trust.
Continuous verification is important to identify and block malicious actions before they happen.
DNG cannot do this, focusing their security model entirely on verification at the start of the user session. All of their security features — authentication, authorization, device checks, trust monitoring — are only utilized when a user begins a session.
However, this means DNG offers no protection after a session has begun. Malicious or negligent user actions will carry through, and any ongoing sessions will not be affected by changes to policy. We tested this by starting a session, changing policy, and seeing if the changed policy affected the ongoing session because the user’s circumstances were no longer considered acceptably secure. Unfortunately, the result was that the ongoing user session could continue to proceed uninhibited.
For more information on why DNG’s security architecture is problematic, read the Perimeter Problem.
Context-Aware Access
And our final pillar: taking institutional context into account when providing access.
It is no longer reasonable to make access decisions based on user identity alone. Instead, access control solutions should have access to data that would better inform the context surrounding otherwise legitimate user activity. The authorization policy should integrate that data into access decisions when deciding if an impending user request should be allowed or denied, completing the full circle of all four pillars to your access solution.
This is known as context-aware access.
DNG attempts to achieve this by having trust monitoring, which is effectively an anomalous behavior detection system. It forms risk profiles for users based on known access patterns, devices, locations, and more. When behaviors change, access requests can be limited by requiring 2FA or outright denied.
While undoubtedly useful, anomalous behavior detection is just a small form of context. DNG’s model also falls short because their security model does not perform continuous verification, meaning their trust monitor only comes into play when users begin a session. Compare this to Pomerium’s full integration model where all information available to the organization can be used to make context-aware access decisions for every single action.
Try Pomerium
Pomerium’s place as an open-source context-aware reverse proxy helps prevent ransomware attacks on internal services and resources. Whether you’re spinning up a new application or trying to add access control to a legacy service, Pomerium builds secure, clientless connections to internal web apps and services without a corporate VPN. The result is:
Easier with clientless access.
Faster by being tunnel-free and deployed where your apps and services are.
Safer because every single action is verified before allowed to execute.
Tailored to your organization’s needs by integrating all data for context-aware access.
Check out our open-source Github Repository or give Pomerium a try today!